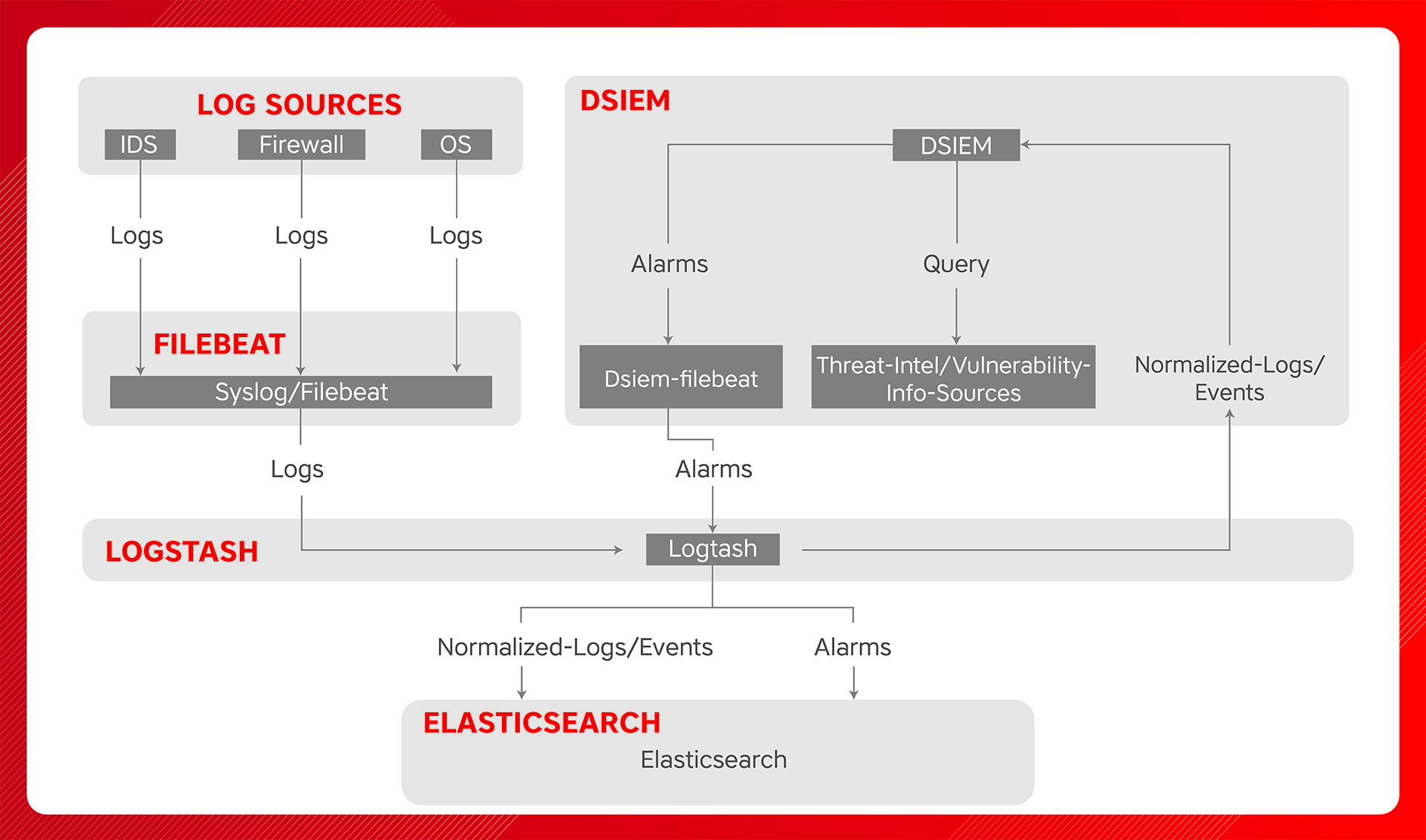
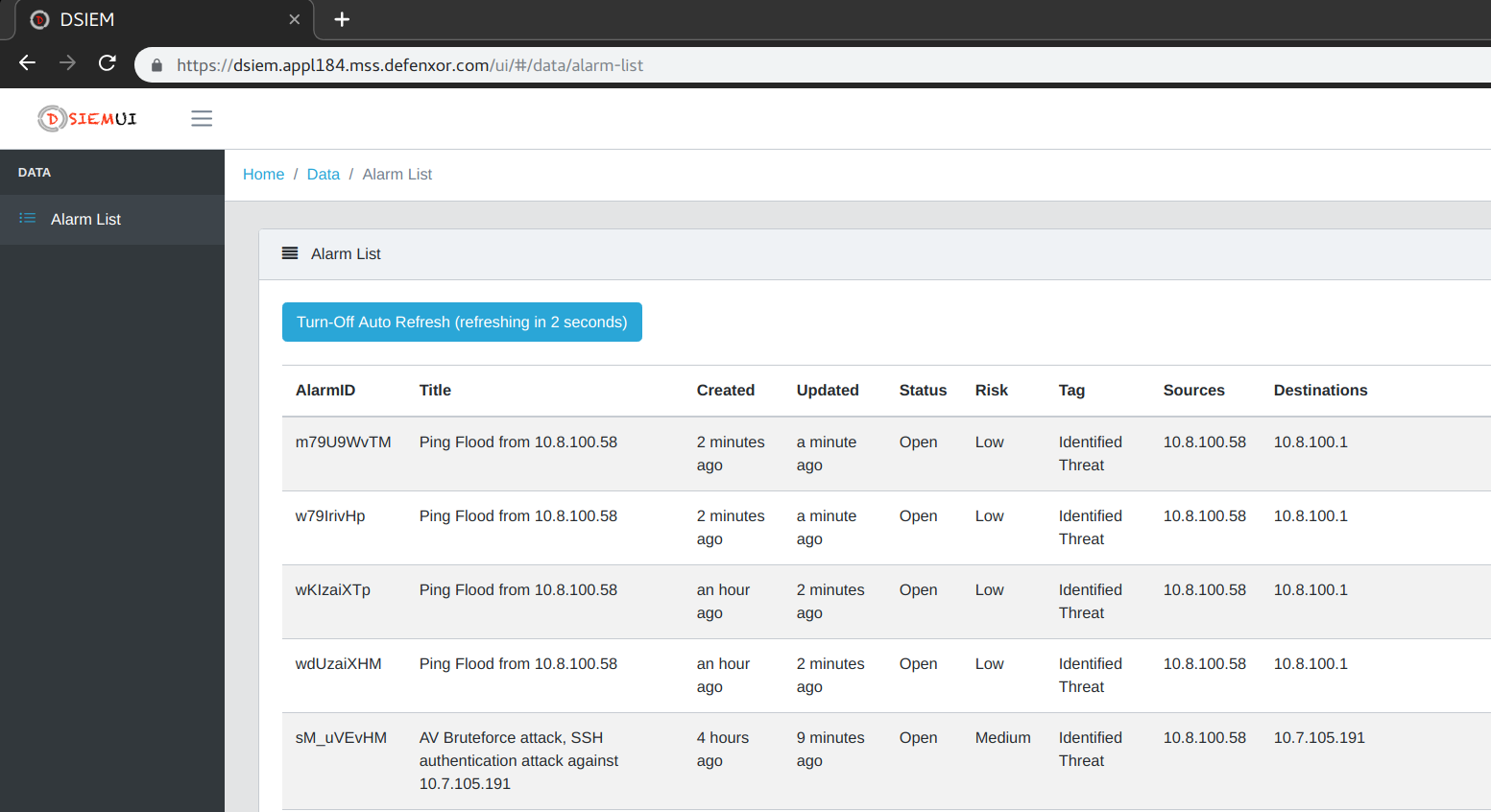
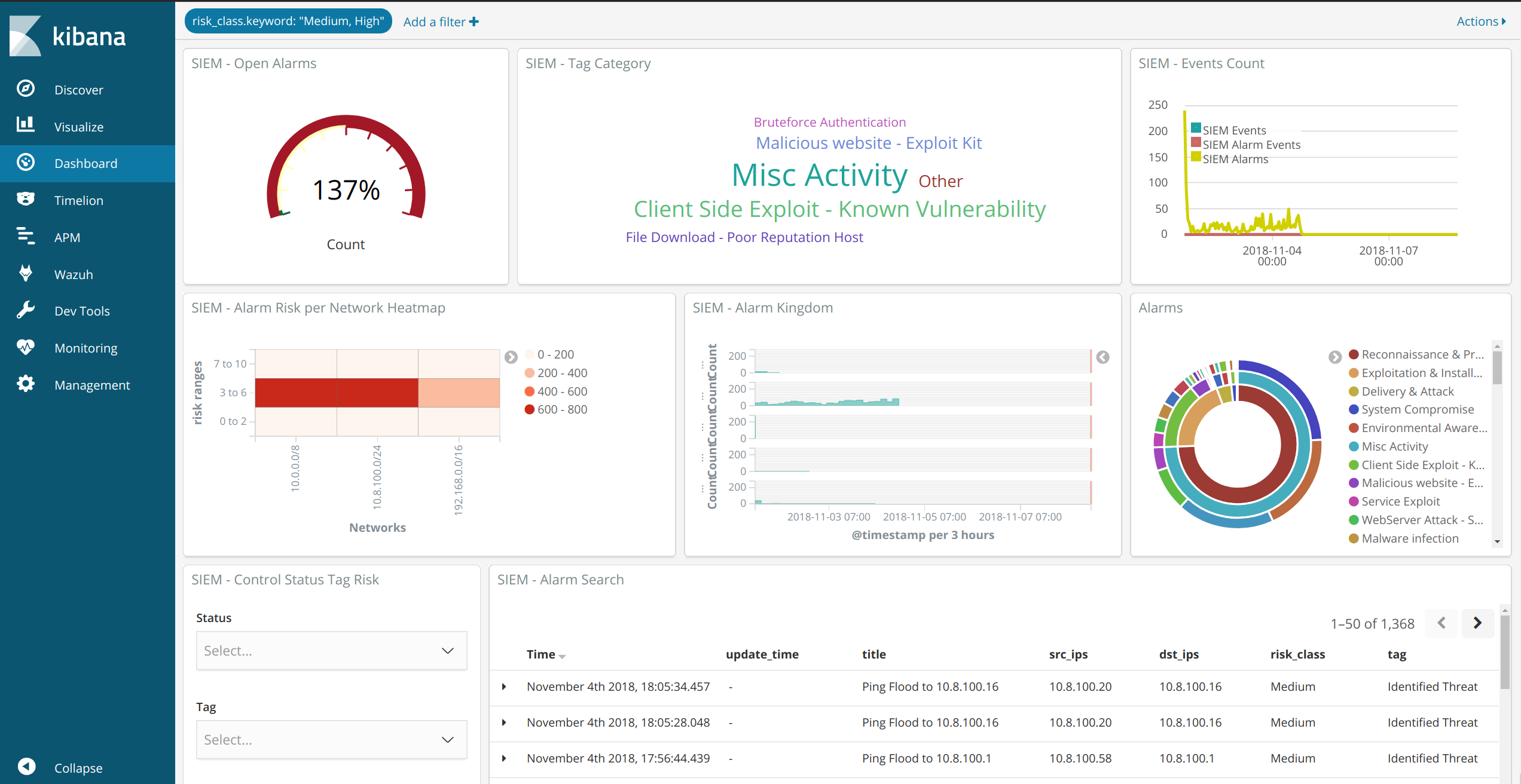
DSIEM provides OSSIM-style correlation for normalized logs/events stored in Elastic platform, queries threat intelligence and vulnerability information sources, and produces risk-adjusted alarms.
Horizontally Scalable
Runs in standalone or clustered mode with NATS as messaging bus between frontend and backend nodes. Along with Elastic, this makes the entire SIEM platform horizontally scalable.
Alarms Enrichment
Enriches alarms with information from threat intelligence and vulnerability information sources. Built-in support for Moloch Wise and Nessus CSV exports. Other sources can be integrated easily through plugins.
Modern Architecture
A cloud-native, 12 factor app, that is loosely-coupled and designed to be composable with other infrastructure platforms. It is even possible to use DSIEM as an OSSIM-style correlation engine for non-Elastic stack.